Security Best Practices for Building HIPAA-Compliant APIs
Healthcare systems move a lot of private data between apps, hospitals, and insurance systems. This data, known as Protected Health Information or PHI, includes details about a patient’s identity, medical history, and treatment.
If PHI is exposed, it can cause serious harm to patients and lead to major legal penalties for the company handling it. That is why any API that processes healthcare data must follow the rules of HIPAA, the Health Insurance Portability and Accountability Act.
This guide explains why PHI must be secured, what company policies help meet HIPAA compliance, and the key technical steps to keep healthcare APIs safe.
For technical reference, see Designing a Unified API Layer for HL7 FHIR Data Exchange.
Why PHI Must Be Protected
PHI includes any information that can identify a person and connects to their health record. Examples are:
- Full name, address, or date of birth
- Medical record and insurance numbers
- Diagnoses, treatments, and prescriptions
- Test results and visit details
This data is valuable to attackers because it can be used for identity theft, insurance fraud, or blackmail. Even a small leak can harm a patient’s privacy and reputation.
In the United States, companies that handle PHI must follow HIPAA regulations. Fines can reach millions of dollars if data is exposed, even by mistake. Beyond penalties, a breach can damage a company’s credibility with patients and partners.
Company Policies for HIPAA Compliance
Technology alone is not enough. To be compliant, the company must also follow clear policies that cover both technical and administrative controls.
Key areas every company must address:
- Access Control
Limit access to PHI only to people who need it for their work. Use individual logins for each user, never shared accounts. - Data Handling Policy
Define how data is stored, transmitted, and backed up. Ensure that all employees understand encryption and secure transfer requirements. - Incident Response Plan
Have a clear process for reporting and responding to security incidents. HIPAA requires that breaches are reported within 60 days. - Employee Training
Every staff member must be trained on how to handle PHI securely, avoid phishing, and follow privacy practices. - Vendor Management
Third parties that process PHI must sign a Business Associate Agreement (BAA). This ensures they also meet HIPAA standards. - Risk Assessment
Perform regular reviews to identify vulnerabilities in APIs, servers, and internal processes. Document all assessments and improvements.
These policies are not optional. They are required under HIPAA’s Administrative, Physical, and Technical Safeguards.
Technical Best Practices for Secure HIPAA APIs
A secure API design combines encryption, authentication, isolation, and auditing. Below are the main technical requirements.
1. Encrypt All Data
Encrypt PHI when stored and when transmitted.
- Use HTTPS with TLS 1.2 or higher for all requests.
- Use AES-256 for database and storage encryption.
- Encrypt backups and logs stored in S3 or similar systems.
Example HTTPS setup in Node.js:
import https from "https";
import fs from "fs";
import app from "./app.js";
const options = {
key: fs.readFileSync("server.key"),
cert: fs.readFileSync("server.crt")
};
https.createServer(options, app).listen(443);
2. Control Access with Roles
Give each user or system only the permissions it needs.
- Use Role-Based Access Control (RBAC)
- Enforce role checks at the API gateway
- Keep access logs for every action
Client --> [Auth Check] --> [Role Validation] --> [Service]
This prevents unauthorized access and limits damage if credentials are stolen.
3. Use Strong Authentication
Use secure token-based authentication such as OAuth2 or JWT.
Tokens should be short-lived and verified on each request.
Example in Python using JWT:
from fastapi import HTTPException
from jose import jwt, JWTError
SECRET_KEY = "replace_with_secure_value"
def verify_token(token: str):
try:
payload = jwt.decode(token, SECRET_KEY, algorithms=["HS256"])
return payload
except JWTError:
raise HTTPException(status_code=401, detail="Invalid token")
Always store secrets and keys in a secure vault.
4. Minimize Data Exposure
Only share what is necessary.
- Filter fields before returning responses
- Never log PHI directly
- Remove identifiers from analytics or training datasets
This limits the impact of data leaks and keeps your API lightweight.
5. Validate All Inputs
Check all request inputs before processing. Reject anything unexpected.
Example:
app.post("/patient", (req, res) => {
const { id, name } = req.body;
if (typeof id !== "string" or typeof name !== "string") {
return res.status(400).json({ error: "Invalid input" });
}
});
Validation protects the API from injection attacks and malformed requests.
6. Log and Audit All Access
Keep detailed audit logs of who accessed what and when.
Store them in secure, immutable storage such as S3.
Audit logs should include timestamp, user ID, endpoint, and action.
Example audit log entry:
{
"timestamp": "2025-11-10T18:22:00Z",
"user": "api_user_14",
"action": "READ_PATIENT",
"endpoint": "/fhir/patient/321",
"status": "200"
}
These records help prove compliance and detect unusual activity.
7. Separate Sensitive Systems
Keep systems that process PHI isolated.
Run them inside private networks with restricted database access.
Use API gateways and firewalls to protect entry points.
Client --> [Gateway] --> [Internal API] --> [Database]
Segmentation keeps external systems from directly reaching PHI databases.
8. Use Secure Messaging
If your system uses Kafka or SQS for data exchange, encrypt every message.
Restrict topic and queue access to trusted services.
Rotate encryption keys automatically.
This protects background data flows that also carry PHI.
9. Monitor and Alert
Monitor your APIs for failed logins, large data exports, or strange access patterns.
Use alerts to notify engineers in real time.
Tracking these patterns helps stop attacks before they become breaches.
10. Regular Testing and Reviews
Conduct security audits, penetration tests, and code reviews.
Scan dependencies for known vulnerabilities.
Update all libraries and frameworks on schedule.
Security must be tested continuously, not only once a year.
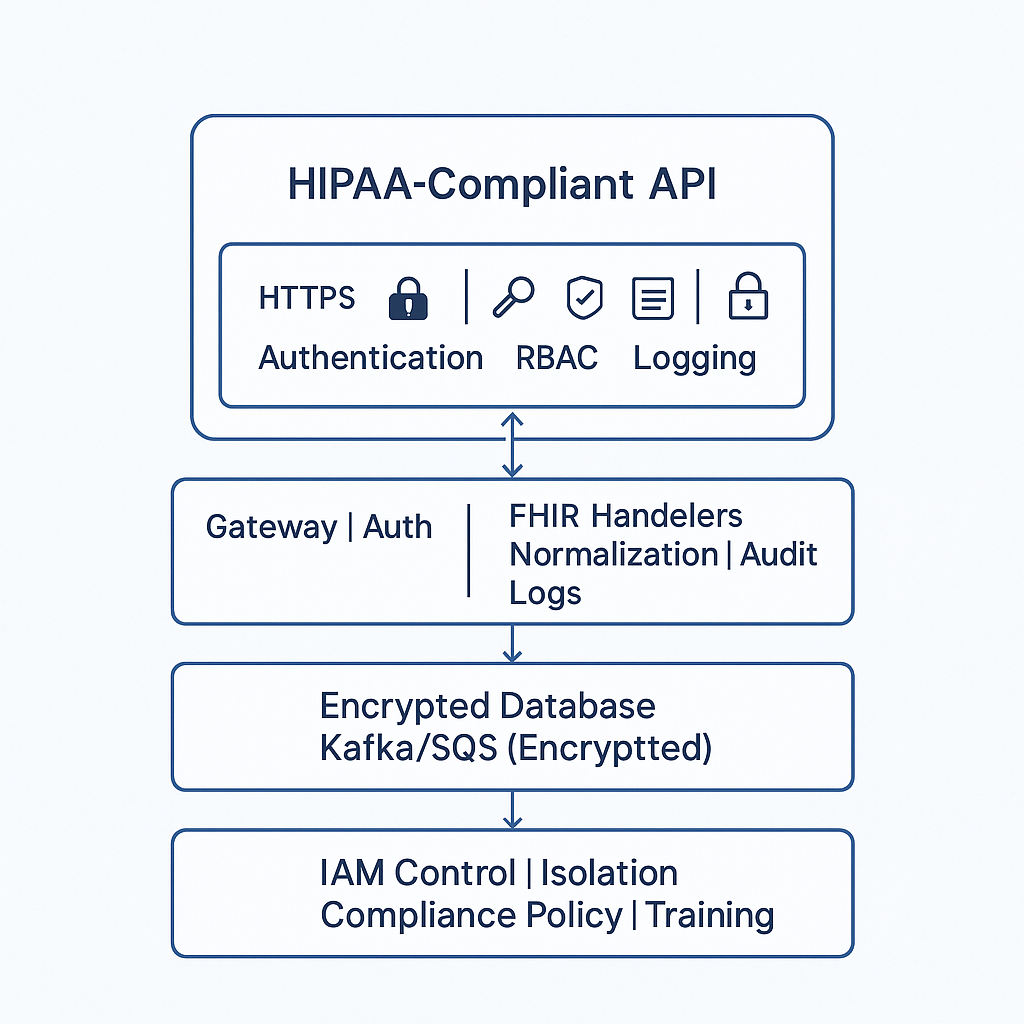
Example Secure HIPAA API Architecture
+--------------------------------------------------------------+
| HIPAA-Compliant API |
+--------------------------------------------------------------+
| HTTPS | OAuth2 | RBAC | Validation | Logging | Monitoring |
+--------------------------------------------------------------+
| Gateway | Auth | FHIR Handlers | Normalization | Audit Logs |
+--------------------------------------------------------------+
| Encrypted Database | Kafka/SQS (Encrypted) | Backup | Alerts |
+--------------------------------------------------------------+
| IAM Control | Isolation | Compliance Policy | Training |
+--------------------------------------------------------------+
Summary
PHI is some of the most sensitive data a system can handle. It includes personal identifiers, health records, and insurance details that can be misused if exposed. Protecting it is not optional.
To comply with HIPAA, companies must build secure APIs and maintain strict internal policies.
Encrypt all data.
Authenticate every user.
Log every action.
Train every employee.
Review risks regularly.
These steps keep patient information safe and ensure that your healthcare API meets the security and privacy expectations set by US law.
For related technical design guidance, see Designing a Unified API Layer for HL7 FHIR Data Exchange.
A well-designed HIPAA-compliant API protects both patients and the company that serves them.

